The Artifice System
A generic and scalable model for Cyber Deception
The National Cyber Deception Laboratory uses the Artifice System to communicate and explore the concept of Cyber Deception.
The Artifice System is a set of models and tools provided by one of the NCDL partners, Artifice and designed by Simon Henderson. When the system is specifically applied to the adversarial context of using Cyber Deception to defend against a network attacker it allows a practitioner to:
- Analyse and operationalise Cyber Deception Campaign goals and determine the desired target behaviour change in network assailants.
- Identify how to assess whether their actions have worked.
- Conduct threat intelligence collection and target analysis to identify vulnerabilities that can be exploited to bring about behaviour change in network attackers.
- Plan Cyber Deception activity and present their ideas in an intellectually robust format.
- Graphically represent Cyber Deception plans to support the communication of deceptive intent to others.
- Execute a Cyber Deception Campaign within a broader enterprise or operational context.
There are two key components to the system:
- A generic framework of 6 psychological attack surfaces for target individuals and groups.
- A set of Deception Gambits to help Cyber Deception Practitioners analyse and design deceptive activity.

Six Block Model
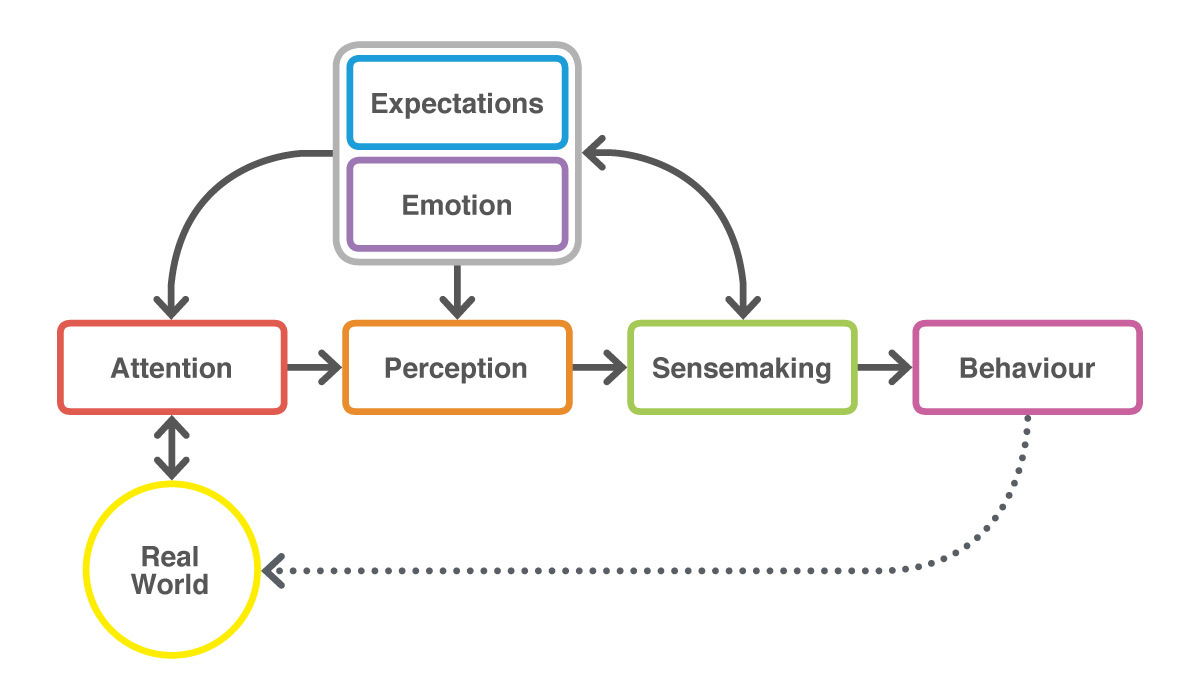
The Artifice System is built around a generic framework called the Six-Block Model. This framework comprises a simplified representation of six core psychological processes that all humans, irrespective of culture, use to make sense of the world and generate action. In this sense, the framework is not specific to the study of adversarial Cyber Deception; however, it does provide a useful and actionable structure for both explaining and designing deceptive action.
In reality, all these processes operate simultaneously in one complex and aggregate activity for making sense of the world and generating action, i.e. ‘thinking’. Everything is connected to everything else, and there is no real notion of ‘flow’ as portrayed. However, separation of the processes into distinct elements, as depicted, helps inform retrospective causal-chain analysis and description of deceptive events; and also provides the basis for a flexible sequence of steps for designing prospective deceptive activity. In this sense, the 6BM constitutes a ‘convenient fiction’ – while it is not ‘true’, it has significant generative utility and provides a firm foundation for the conceptualisation of deception and influence in an adversarial context.
For the purposes of analysis and planning, the processes portrayed in the model are treated as acting interdependently. Attention steers perception, perception feeds sensemaking, sensemaking generates expectations and emotions (that in turn shape other processes), and sensemaking also drives behaviour.
Each process represents an attack surface that can be targeted and influenced independently to achieve different kinds of effect on the target’s thinking and behaviour. However, influencing interdependent processes is contingent on influencing proceeding processes, i.e. later processes can only be influenced by controlling the earlier processes that impact on them – for example, a target’s sensemaking can only be influenced by first controlling the target’s attention, and then shaping its perception.
The NCDL uses the Six Block Model to:
- Help structure thinking systematically about different kinds of Cyber Deception, and the effects sought.
- Provide a structure for collecting on and analysing a target to discover opportunities for influencing and deceiving them.
- Support the representation and analysis of retrospective or prospective cases of Cyber Deception.
- Provide a structure for working through a series of considerations that underpin the design (and planning) of Cyber Deception activity.
- Provide an index to help sort different strategies that can be incorporated into a plan for fooling a network attacker.
- Support the measurement of the effectiveness of a Cyber Deception course of action.
- Support a counter-deception process that aids the detection of deception used by attackers against defenders of networks.
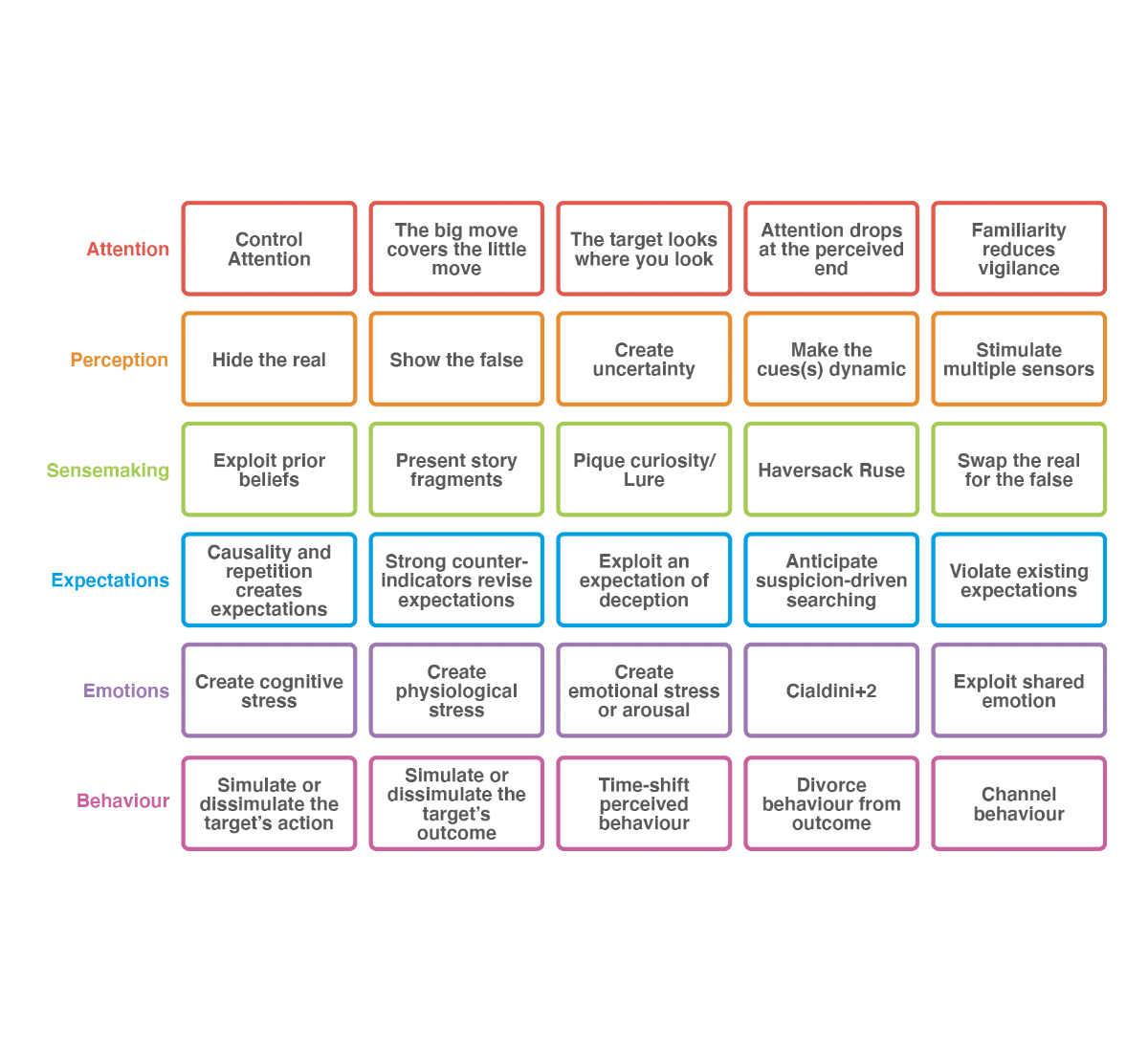
Deception Gambits
Gambit: a device or action, typically one entailing a degree of risk, that is calculated to gain an advantage.
The term ‘gambit’ is used as all deception involves risk. Relying on a Cyber Deception strategy increases risk compared to not relying on a deceptive strategy, because the attacker gets a choice over what course of action they ultimately take.
The Artifice Gambits are primitive deceptive thinking ‘seeds’, designed to support the Cyber Deception Planner. The gambits are target independent and can therefore be used to manipulate the components of any target’s 6BM. The gambits provide a set of linkable ‘building blocks’, that can be combined in different ways to achieve different kinds of impacts and effects.